Inglese
🪨 Standing Stones
🪨 Standing Stones
Stonehenge

Stonehenge (pietra sospesa, da stone, pietra, e henge, che deriva da hang, sospendere: in riferimento agli architravi) è un sito neolitico che si trova vicino ad Amesbury nello Wiltshire, Inghilterra, circa 13 chilometri a nord-ovest di Salisbury.
È il più celebre e imponente cromlech («circolo di pietra»): composto da un insieme circolare di colossali pietre erette, conosciute come megaliti, sormontate da consistenti architravi orizzontali di collegamento di cui alcune sono in quota ed è uno dei più antichi sistemi trilitici conosciuti (trilitico: sistema costituito da tri = tre + lithos = pietra, due montanti verticali ed un architrave orizzontale).
Ipotizzando che l'attuale allineamento riproduca fedelmente il precedente, alcuni sostengono che Stonehenge rappresenti un "antico osservatorio astronomico", con un significato particolare ai punti di solstizio ed equinozio, anche se l'importanza del suo uso per tale scopo è dibattuta.
Oltre che meta del turismo di massa, Stonehenge è luogo di pellegrinaggio per molti seguaci del celtismo, della wicca e di altre religioni neopagane, e fu teatro di un festival musicale libero tra il 1972 e il 1984.
Translation
Translation
Stonehenge is a prehistoric monument on Salisbury Plain in Wiltshire, England, two miles (3 km) west of Amesbury.
It consists of an outer ring of vertical sarsen standing stones, each around 13 feet (4.0 m) high, seven feet (2.1 m) wide, and weighing around 25 tons, topped by connecting horizontal lintel stones. Inside is a ring of smaller bluestones. Inside these are free-standing trilithons, two bulkier vertical Sarsens joined by one lintel. The whole monument, now ruinous, is aligned towards the sunrise on the summer solstice.
Archaeologists believe that Stonehenge was constructed from 3000 BC to 2000 BC. One of the most famous landmarks in the United Kingdom, Stonehenge is regarded as a British cultural icon. It has been a legally protected Scheduled Ancient Monument since 1882, when legislation to protect historic monuments was first successfully introduced in Britain. The site and its surroundings were added to UNESCO's list of World Heritage Sites in 1986. Stonehenge is owned by the Crown and managed by English Heritage.
The Nine Ladies

The Nine Ladies is a stone circle located on Stanton Moor in Derbyshire in the English East Midlands. The Nine Ladies is part of a tradition of stone circle construction that spread throughout much of Britain, Ireland, and Brittany during the Late Neolithic and Early Bronze Ages, over a period between 3300 and 900 BCE. The purpose of such monuments is unknown, although archaeologists speculate that the stones represented supernatural entities for the circles' builders.
Measuring 10.8 metres in diameter, the stone circle consists of ten millstone grit stones, although for several centuries one of these was buried, providing the impression that there had been nine stones. Whether the tenth was part of the original prehistoric design or a later addition is unknown. A single monolith, the King Stone, stands to the southwest of the circle; it is unknown if this was placed there in deliberate reference to the Nine Ladies circle or whether their proximity is incidental.
Roll Right Stones

The Rollright Stones are a complex of three Neolithic and Bronze Age megalithic monuments near the village of Long Compton, on the borders of Oxfordshire and Warwickshire.
They were built at different periods in late prehistory. During the period when the three monuments were erected, there was a continuous tradition of ritual behaviour on sacred ground, from the 4th to the 2nd millennium BCE.
The first to be constructed was the Whispering Knights, a dolmen that dates to the Early or Middle Neolithic period. It was likely to have been used as a place of burial. This was followed by the King's Men, a stone circle that was constructed in the Late Neolithic or Early Bronze Age, it has parallels to other circles located further north, in the Lake District, implying a trade-based or ritual connection. The third monument, the King Stone, is a single monolith.
By the Early Modern period, folkloric stories had developed about the Stones, telling of how they had once been a king and his knights who had been turned to stone by a witch. Such stories continued to be taught amongst local people well into the 19th century.
In the 20th century, the stones became an important site for adherents of various forms of Contemporary Paganism, as well as for other esotericists, who hold magico-religious ceremonies there. They also began to be referred to more widely in popular culture, being featured in television, literature, music and art.
Avebury

Ad Avebury, nella contea inglese dello Wiltshire, nei dintorni dell'omonimo villaggio, si trovano un grande henge e numerosi cerchi di pietre. Si tratta di uno dei monumenti neolitici europei meglio conservati ed è databile attorno a 5000 anni fa. È più antico del sito megalitico di Stonehenge, che si trova a circa 32 km a sud, anche se i due siti sono quasi contemporanei. Si trova approssimativamente a metà strada tra Marlborough e Calne, poco distante dalla A4 a nord della A361 verso Wroughton.
Avebury è di proprietà della National Trust.
Translation
Translation
Avebury is a Neolithic henge monument containing three stone circles, around the village of Avebury in Wiltshire, in southwest England. One of the best known prehistoric sites in Britain, it contains the largest megalithic stone circle in the world. It is both a tourist attraction and a place of religious importance to contemporary pagans.
Constructed over several hundred years in the third millennium BC, during the Neolithic, or New Stone Age, the monument comprises a large henge (a bank and a ditch) with a large outer stone circle and two separate smaller stone circles situated inside the centre of the monument.
Avebury is owned and managed by the National Trust. It has been designated a Scheduled Ancient Monument, as well as a World Heritage Site, in the latter capacity being seen as a part of the wider prehistoric landscape of Wiltshire known as Stonehenge, Avebury and Associated Sites.
Resources
Resources
⚔️ The Falkland/Malvinas War
⚔️ The Falkland/Malvinas War
La guerra delle Falkland o guerra delle Malvine fu un conflitto militare combattuto tra aprile e giugno 1982 tra Argentina e Regno Unito per il controllo e il possesso delle isole Falkland e della Georgia del Sud e Isole Sandwich Australi.
Alla vigilia della guerra l'Argentina si trovava nel pieno di una devastante crisi economica e di una contestazione civile su larga scala contro la giunta militare che governava il Paese. Il governo, guidato dal generale Leopoldo Galtieri, l'allora presidente, decise di giocare la carta del sentimento nazionalistico lanciando quella che considerava una guerra facile e veloce per reclamare le Falkland, su cui l'Argentina (che le chiama Malvinas, Malvine) rivendicava la sovranità. Sebbene colto di sorpresa dall'attacco, il Regno Unito organizzò una task force navale per respingere le forze argentine che avevano occupato gli arcipelaghi. Dopo pesanti combattimenti, i britannici prevalsero e le isole tornarono sotto il controllo del Regno Unito.
Le conseguenze politiche della guerra furono profonde: in Argentina crebbero dissenso e proteste contro il governo militare, avviandolo alla caduta definitiva, mentre un'ondata di patriottismo si diffuse nel Regno Unito, ridando forza al governo del primo ministro Margaret Thatcher. Il vittorioso conflitto diede fiato alle ambizioni britanniche di potenza post imperiale (dopo la grave delusione seguita alla decolonizzazione), dimostrando che il Regno Unito aveva ancora la capacità di proiettare con successo la propria potenza militare anche in una guerra a enorme distanza dalla madrepatria.
Translation
Translation
The Falklands War was a ten-week undeclared war between Argentina and the United Kingdom in 1982 over two British dependent territories in the South Atlantic: the Falkland Islands and its territorial dependency, South Georgia and the South Sandwich Islands.
The conflict began on 2 April, when Argentina invaded and occupied the Falkland Islands, followed by the invasion of South Georgia the next day. The British government dispatched a naval task force to engage the Argentine Navy and Air Force before making an amphibious assault on the islands. The conflict lasted 74 days and ended with an Argentine surrender on 14 June, returning the islands to British control. In total, 649 Argentine military personnel, 255 British military personnel, and three Falkland Islanders died during the hostilities.
The conflict was a major episode in the protracted dispute over the territories' sovereignty. Argentina asserted (and maintains) that the islands are Argentine territory, and the Argentine government thus characterised its military action as the reclamation of its own territory. The British government regarded the action as an invasion of a territory that had been a Crown colony since 1841. Falkland Islanders, who have inhabited the islands since the early 19th century, are predominantly descendants of British settlers, and strongly favour British sovereignty. Neither state officially declared war, although both governments declared the islands a war zone.
The conflict has had a strong effect in both countries and has been the subject of various books, articles, films, and songs. Patriotic sentiment ran high in Argentina, but the unfavourable outcome prompted large protests against the ruling military government, hastening its downfall and the democratisation of the country. In the United Kingdom, the Conservative government, bolstered by the successful outcome, was re-elected with an increased majority the following year. The cultural and political effect of the conflict has been less in the UK than in Argentina, where it has remained a common topic for discussion.
Resources
Resources
🤖 AI
🤖 AI
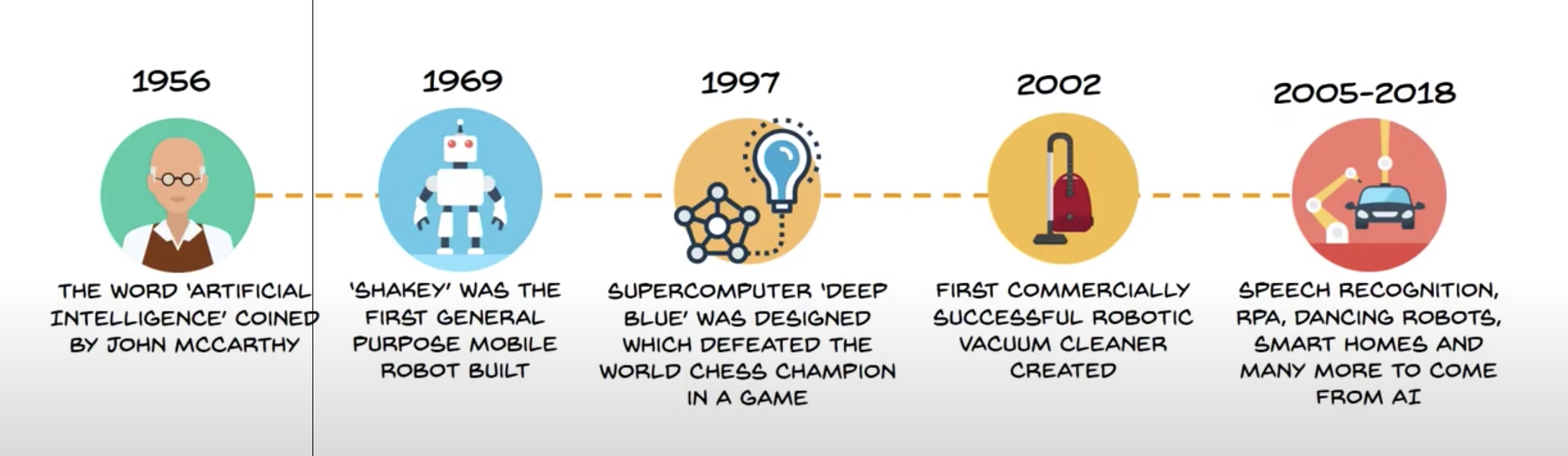
History
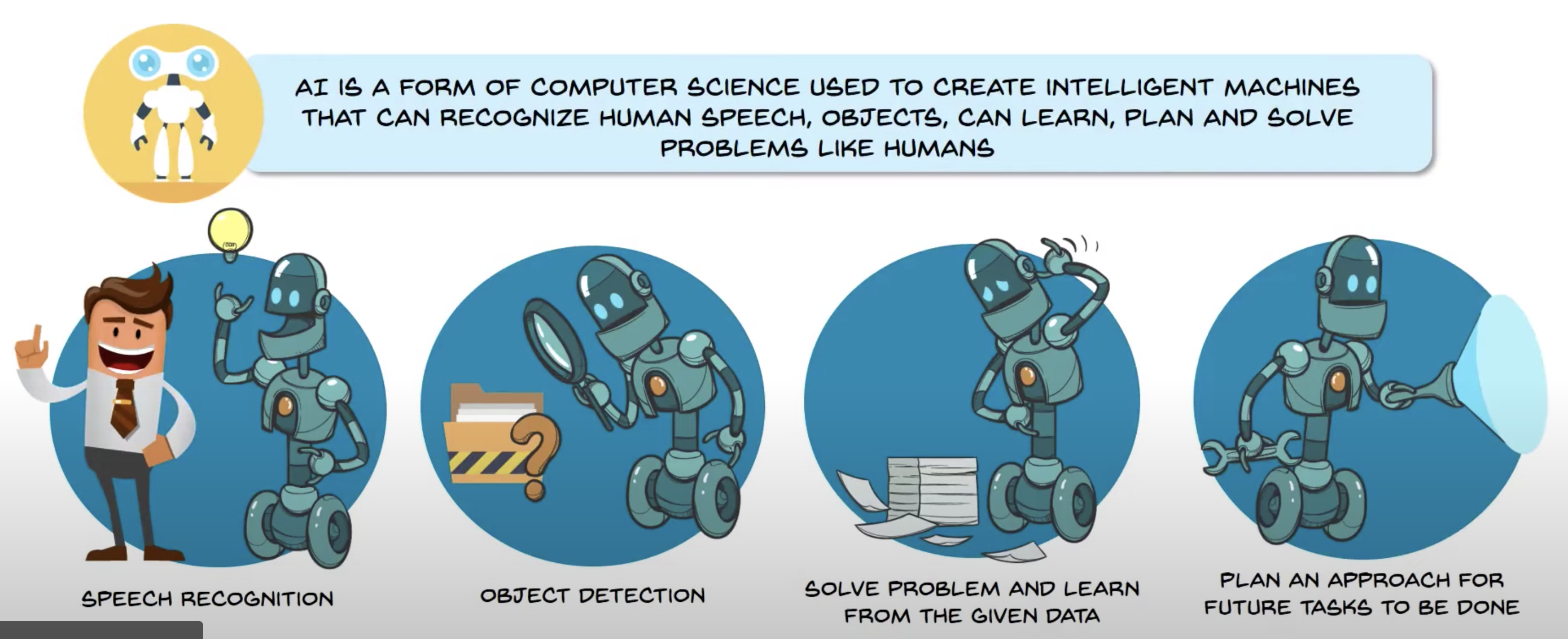
What is it?
Different types
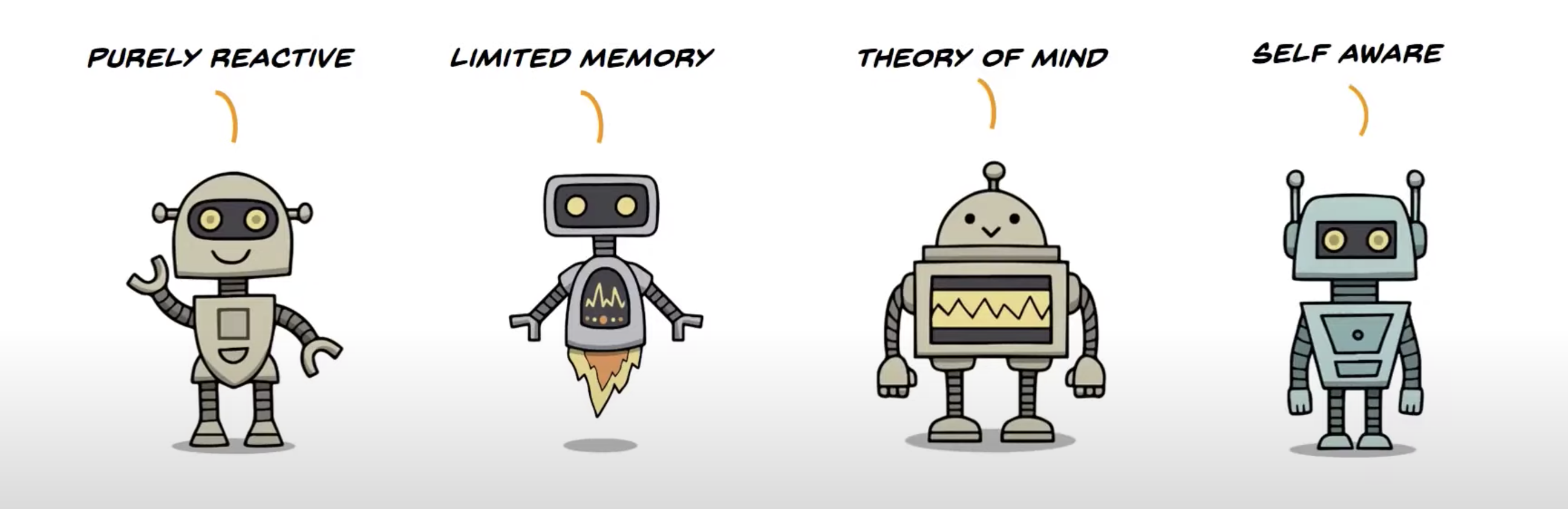
- Purely reactive: just reacts to some inputs (chess)
- Limited memory: uses some kind of data to create useful suggestions or intelligent answers
- Theory of mind: has the capacity to understand thoughts and emotions and interact socially (still in the process of being invented
- Self aware: (not invented yet)
Applications of AI
- Banking Fraud Detection
- Online customer support
- Cyber security
- Virtual Assistants
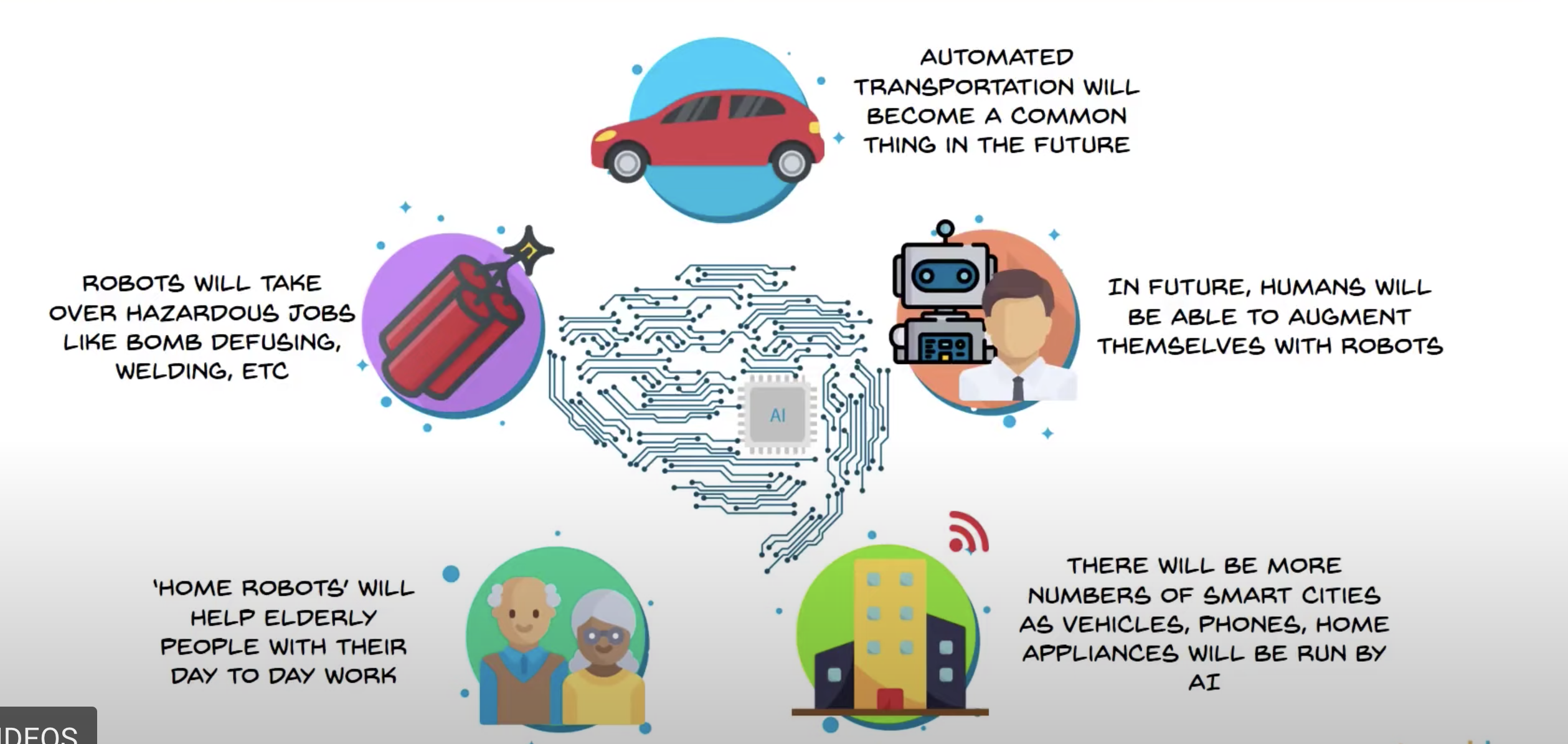
The future
Resources
Resources
💡 The development of computers
💡 The development of computers
Diagram
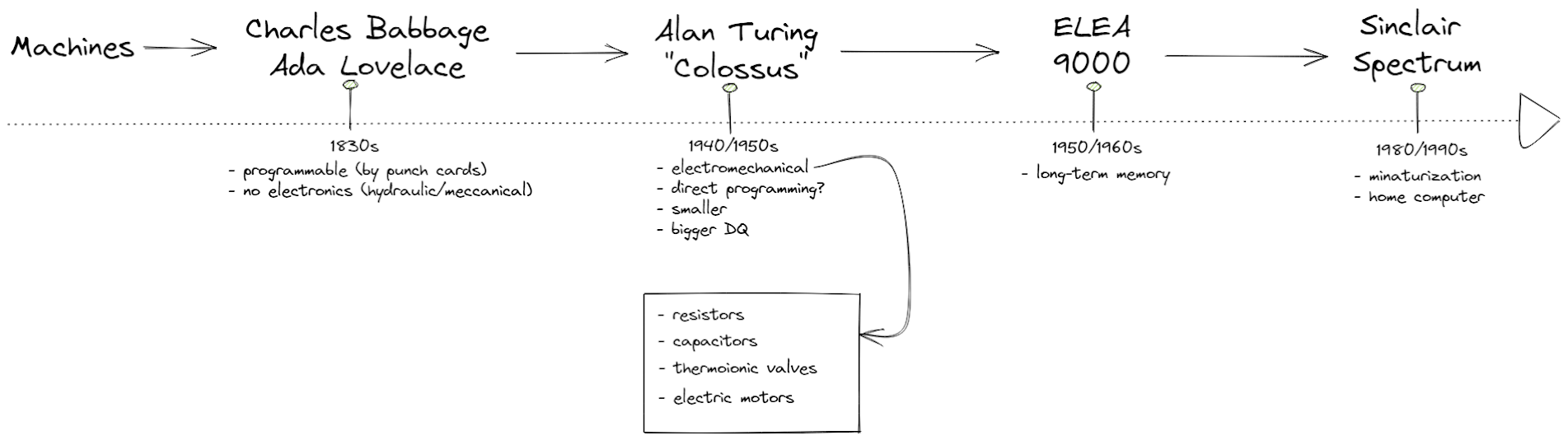
Analytical engine
La macchina analitica (Analytical engine in inglese) è stato il primo prototipo di un computer meccanico sviluppato per eseguire compiti generici. Il progetto fu sviluppato dal matematico, filosofo e scienziato inglese Charles Babbage (1791–1871), che cercò anche di realizzarlo praticamente. Rappresenta un importante passo nella storia dell'informatica.
Translation
Translation
The Analytical Engine was a proposed mechanical general-purpose computer designed by English mathematician and computer pioneer Charles Babbage. It was first described in 1837 as the successor to Babbage's difference engine, which was a design for a simpler mechanical calculator.
The Analytical Engine incorporated an arithmetic logic unit, control flow in the form of conditional branching and loops, and integrated memory, making it the first design for a general-purpose computer that could be described in modern terms as Turing-complete.
In other words, the logical structure of the Analytical Engine was essentially the same as that which has dominated computer design in the electronic era The Analytical Engine is one of the most successful achievements of Charles Babbage.
Babbage was never able to complete construction of any of his machines due to conflicts with his chief engineer and inadequate funding.
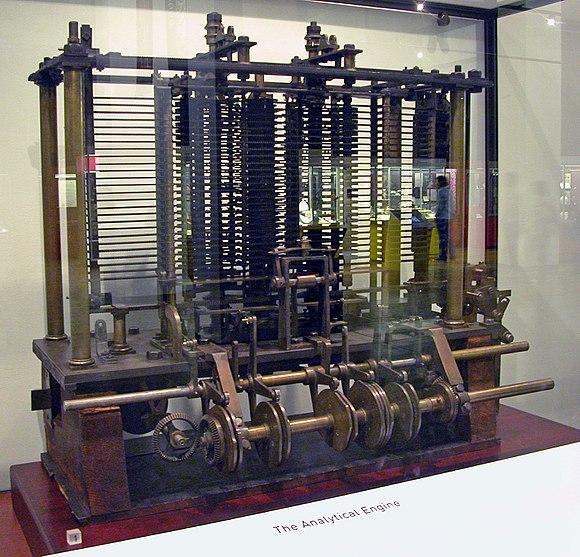
Colossus
Il Colossus è stato uno dei primi computer elettronici programmabili nella storia dell'informatica. Costruito e messo in opera nel Regno Unito, durante la seconda guerra mondiale, fu in grado di decifrare i codici sviluppati dalla cifratrice Lorenz SZ 40/42 usata dai nazisti per proteggere la corrispondenza fra Adolf Hitler e i suoi capi di stato maggiore, oltre che alle comunicazioni Purple e Red giapponesi, basate sulla tecnologia di Enigma.
I servizi segreti britannici fecero di tutto per interpretare i codici dei nazisti, che però venivano cambiati quotidianamente.
Il Colossus, costruito in segreto per la Royal Navy, è stato il primo a usare le valvole termoioniche, fino ad allora usate solo da amplificatori, al posto dei relè: sfruttandone ben 1500, fu in grado di aumentare notevolmente la potenza di calcolo.
Il suo primato cronologico, tuttavia, è stato riconosciuto in ritardo a causa del rigoroso segreto imposto dal Regno Unito, resistito per decenni anche dopo la conclusione della guerra.
Translation
Translation
Colossus was a set of computers developed by British codebreakers in the years 1943–1945 to help in the cryptanalysis of the Lorenz cipher. Colossus used thermionic valves (vacuum tubes) to perform Boolean and counting operations. Colossus is thus regarded as the world's first programmable, electronic, digital computer, although it was programmed by switches and plugs and not by a stored program.
Colossus was designed by General Post Office (GPO) research telephone engineer Tommy Flowers to solve a problem posed by mathematician Max Newman at the Government Code and Cypher School (GC&CS) at Bletchley Park. Alan Turing's use of probability in cryptanalysis contributed to its design. It has sometimes been erroneously stated that Turing designed Colossus to aid the cryptanalysis of the Enigma. (Turing's machine that helped decode Enigma was the electromechanical Bombe, not Colossus.)
Use of these machines allowed the Allies to obtain a vast amount of high-level military intelligence from intercepted radiotelegraphy messages between the German High Command (OKW) and their army commands throughout occupied Europe.
The existence of the Colossus machines was kept secret until the mid-1970s. All but two machines were dismantled into such small parts that their use could not be inferred. The two retained machines were eventually dismantled in the 1960s.
Elea 9000
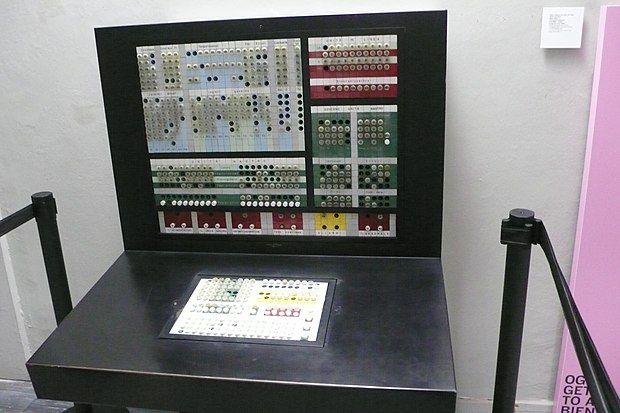
Elea è il nome di una serie di elaboratori elettronici mainframe sviluppati da Olivetti nella seconda metà degli anni cinquanta la cui terza generazione, denominata Elea 9003, fu il primo della storia interamente realizzato con componenti a stato solido. Fu concepito, progettato e sviluppato da un piccolo gruppo di giovani ricercatori guidati da Mario Tchou.
Fu commercializzato alcuni mesi dopo l'uscita del concorrente 2002 della Siemens, che, però, ancora utilizzava alcune valvole, e vari mesi prima del lancio del 7090, il primo computer interamente a transistor realizzato dalla IBM.
L'acronimo ELEA stava per Elaboratore Elettronico Aritmetico (quest'ultimo aggettivo poi modificato in "Automatico" per ragioni di marketing).
Translation
Translation
The Elea 9003 is one of a series of mainframe computers Olivetti developed starting in the late 1950s. The system, made entirely with transistors for high performance, was conceived, designed and developed by a small group of researchers led by Mario Tchou (1924–1961).
It was the first solid-state computer designed and manufactured in Italy.
The acronym ELEA stood for Elaboratore Elettronico Aritmetico (Arithmetical Electronic Computer, then changed to Elaboratore Elettronico Automatico for marketing reasons).
Sinclair Spectrum
Lo ZX Spectrum è un home computer creato e prodotto dal 1982 fino al 1986 dalla Sinclair Research Ltd, e dal 1986 al 1992 dalla Amstrad.
In Europa fu il principale antagonista del Commodore 64 e conquistò un discreto settore di mercato grazie ad un prezzo di listino più economico; infatti le piccole dimensioni, la velocità di calcolo e il prezzo relativamente basso lo resero popolare negli anni ottanta in vari Stati del mondo.

Translation
Translation
The ZX Spectrum is an 8-bit personal home computer developed by Sinclair Research. It was first released in the United Kingdom on 23 April 1982 and went on to become Britain's best-selling microcomputer.
Referred to during development as the ZX81 Colour and ZX82, it was launched as the ZX Spectrum to highlight the machine's colour display, compared with the black and white display of its predecessor, the ZX81. The Spectrum was released as eight different models, altogether they sold over 5 million units worldwide.
The Spectrum was among the first home computers in the United Kingdom aimed at a mainstream audience, similar in significance to the Commodore 64 in the US or the MO5 in France. The introduction of the ZX Spectrum led to a boom in companies producing software and hardware for the machine, the effects of which are still seen.
The machine was officially discontinued in 1992.
📠 Alan Turing e la macchina Enigma
📠 Alan Turing e la macchina Enigma
Alan Turing

Alan Mathison Turing (Londra 1912 – Manchester 1954) è stato un matematico, logico, crittografo e filosofo britannico, considerato uno dei padri dell'informatica e uno dei più grandi matematici del XX secolo.
Il suo lavoro ebbe una vasta influenza sulla nascita della disciplina dell'informatica, grazie alla sua formalizzazione dei concetti di algoritmo e calcolo mediante l'omonima macchina, che a sua volta costituì un significativo passo avanti nell'evoluzione verso il moderno computer.
Per questo contributo è solitamente considerato il padre della scienza informatica e dell'intelligenza artificiale, da lui teorizzate già negli anni trenta del '900, ed anche uno dei più brillanti crittoanalisti che operarono nel Regno Unito durante la seconda guerra mondiale, per decifrare i messaggi scambiati da diplomatici e militari delle Potenze dell'Asse.
Turing lavorò infatti a Bletchley Park, il principale centro di crittoanalisi del Regno Unito, dove ideò una serie di tecniche per violare i cifrari tedeschi, incluso l'utilizzo di una macchina elettromeccanica (chiamata "Bomba") in grado di decodificare codici creati dalla macchina crittografica Enigma. Morì, suicida, a soli 41 anni.
Translation
Translation
Alan Mathison Turing OBE FRS (1912 – 1954) was an English mathematician, computer scientist, logician, cryptanalyst, philosopher, and theoretical biologist. Turing was highly influential in the development of theoretical computer science, providing a formalisation of the concepts of algorithm and computation with the Turing machine, which can be considered a model of a general-purpose computer. He is widely considered to be the father of theoretical computer science and artificial intelligence.
In 1938, he obtained his PhD from the Department of Mathematics at Princeton University. During the Second World War, Turing worked for the Government Code and Cypher School (GC&CS) at Bletchley Park, Britain's codebreaking centre that produced Ultra intelligence. For a time he led Hut 8, the section that was responsible for German naval cryptanalysis. Here, he devised a number of techniques for speeding the breaking of German ciphers, including improvements to the pre-war Polish bombe method, an electromechanical machine that could find settings for the Enigma machine. Turing played a crucial role in cracking intercepted coded messages that enabled the Allies to defeat the Axis powers in many crucial engagements, including the Battle of the Atlantic.
Turing was prosecuted in 1952 for homosexual acts. He accepted hormone treatment with DES, a procedure commonly referred to as chemical castration, as an alternative to prison. Turing died on 7 June 1954 from cyanide poisoning. An inquest determined his death as a suicide, but it has been noted that the known evidence is also consistent with accidental poisoning.
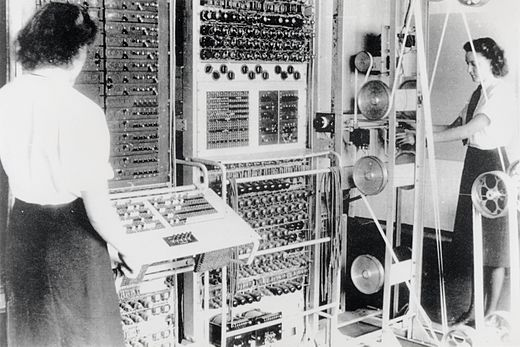
Enigma

Enigma fu un dispositivo elettromeccanico per cifrare e decifrare messaggi. Macchina nata da un tentativo di commercializzazione poi fallito, fu ampiamente utilizzata dalle forze armate tedesche durante il periodo nazista e della seconda guerra mondiale. La facilità d'uso e la presunta indecifrabilità furono le maggiori ragioni del suo ampio utilizzo.
Nonostante fosse stata modificata e potenziata nell'arco del suo periodo di utilizzo, un nutrito gruppo di esperti riuscì a violarla dopo essersi impegnato a lungo con questo intento. I primi a decifrarla nel 1932 furono alcuni matematici polacchi: Marian Rejewski, Jerzy Różycki e Henryk Zygalski. Il loro lavoro ha permesso di ottenere ulteriori informazioni sulla sempre più aggiornata macchina dei tedeschi "Enigma", prima in Polonia e, dopo lo scoppio della guerra, anche in Francia e Gran Bretagna. La decrittazione dei messaggi cifrati con Enigma fornì per quasi tutta la seconda guerra mondiale importantissime informazioni alle forze alleate.
Translation
Translation
The Enigma machine is a cipher device developed and used in the early- to mid-20th century to protect commercial, diplomatic, and military communication. It was employed extensively by Nazi Germany during World War II, in all branches of the German military. The Enigma machine was considered so secure that it was used to encipher the most top-secret messages.
The Enigma has an electromechanical rotor mechanism that scrambles the 26 letters of the alphabet. In typical use, one person enters text on the Enigma's keyboard and another person writes down which of the 26 lights above the keyboard illuminated at each key press. If plain text is entered, the illuminated letters are the ciphertext. Entering ciphertext transforms it back into readable plaintext. The rotor mechanism changes the electrical connections between the keys and the lights with each keypress.
The security of the system depends on machine settings that were generally changed daily, based on secret key lists distributed in advance, and on other settings that were changed for each message. The receiving station would have to know and use the exact settings employed by the transmitting station to successfully decrypt a message.
While Nazi Germany introduced a series of improvements to the Enigma over the years, and these hampered decryption efforts, they did not prevent Poland from cracking the machine prior to the war, enabling the Allies to exploit Enigma-enciphered messages as a major source of intelligence.
Resources
Resources
🦠 Ransomware
🦠 Ransomware
Ransomware is a type of malware from cryptovirology that threatens to publish the victim's personal data or perpetually block access to it unless a ransom is paid. While some simple ransomware may lock the system without damaging any files, more advanced malware uses a technique called cryptoviral extortion. It encrypts the victim's files, making them inaccessible, and demands a ransom payment to decrypt them. In a properly implemented cryptoviral extortion attack, recovering the files without the decryption key is an intractable problem – and difficult to trace digital currencies such as paysafecard or Bitcoin and other cryptocurrencies are used for the ransoms, making tracing and prosecuting the perpetrators difficult.
Ransomware attacks are typically carried out using a Trojan disguised as a legitimate file that the user is tricked into downloading or opening when it arrives as an email attachment. However, one high-profile example, the WannaCry worm, traveled automatically between computers without user interaction.
Starting as early as 1989 with the first documented ransomware known as the AIDS trojan, the use of ransomware scams has grown internationally. There were 181.5 million ransomware attacks in the first six months of 2018. This record marks a 229% increase over this same time frame in 2017. In June 2014, vendor McAfee released data showing that it had collected more than double the number of ransomware samples that quarter than it had in the same quarter of the previous year. CryptoLocker was particularly successful, procuring an estimated US$3 million before it was taken down by authorities, and CryptoWall was estimated by the US Federal Bureau of Investigation (FBI) to have accrued over US$18 million by June 2015. In 2020, the IC3 received 2,474 complaints identified as ransomware with adjusted losses of over $29.1 million. The losses could be more than that, according to the FBI. According to a report by SonicWall, there were around 623 million ransomware attacks in 2021.
Operation
The concept of file-encrypting ransomware was invented and implemented by Young and Yung at Columbia University and was presented at the 1996 IEEE Security & Privacy conference. It is called cryptoviral extortion and it was inspired by the fictional facehugger in the movie Alien. Cryptoviral extortion is the following three-round protocol carried out between the attacker and the victim.
[attacker→victim] The attacker generates a key pair and places the corresponding public key in the malware. The malware is released.
[victim→attacker] To carry out the cryptoviral extortion attack, the malware generates a random symmetric key and encrypts the victim's data with it. It uses the public key in the malware to encrypt the symmetric key. This is known as hybrid encryption and it results in a small asymmetric ciphertext as well as the symmetric ciphertext of the victim's data. It zeroizes the symmetric key and the original plaintext data to prevent recovery. It puts up a message to the user that includes the asymmetric ciphertext and how to pay the ransom. The victim sends the asymmetric ciphertext and e-money to the attacker.
[attacker→victim] The attacker receives the payment, deciphers the asymmetric ciphertext with the attacker's private key, and sends the symmetric key to the victim. The victim deciphers the encrypted data with the needed symmetric key thereby completing the cryptovirology attack.
The symmetric key is randomly generated and will not assist other victims. At no point is the attacker's private key exposed to victims and the victim need only send a very small ciphertext (the encrypted symmetric-cipher key) to the attacker.
Ransomware attacks are typically carried out using a Trojan, entering a system through, for example, a malicious attachment, embedded link in a Phishing email, or a vulnerability in a network service. The program then runs a payload, which locks the system in some fashion, or claims to lock the system but does not (e.g., a scareware program). Payloads may display a fake warning purportedly by an entity such as a law enforcement agency, falsely claiming that the system has been used for illegal activities, contains content such as pornography and "pirated" media.
Some payloads consist simply of an application designed to lock or restrict the system until payment is made, typically by setting the Windows Shell to itself, or even modifying the master boot record and/or partition table to prevent the operating system from booting until it is repaired. The most sophisticated payloads encrypt files, with many using strong encryption to encrypt the victim's files in such a way that only the malware author has the needed decryption key.
Payment is virtually always the goal, and the victim is coerced into paying for the ransomware to be removed either by supplying a program that can decrypt the files, or by sending an unlock code that undoes the payload's changes. While the attacker may simply take the money without returning the victim's files, it is in the attacker's best interest to perform the decryption as agreed, since victims will stop sending payments if it becomes known that they serve no purpose. A key element in making ransomware work for the attacker is a convenient payment system that is hard to trace. A range of such payment methods have been used, including wire transfers, premium-rate text messages, pre-paid voucher services such as paysafecard, and the Bitcoin cryptocurrency.
In May 2020, vendor Sophos reported that the global average cost to remediate a ransomware attack (considering downtime, people time, device cost, network cost, lost opportunity and ransom paid) was $761,106. Ninety-five percent of organizations that paid the ransom had their data restored.
Mitigation
If an attack is suspected or detected in its early stages, it takes some time for encryption to take place; immediate removal of the malware (a relatively simple process) before it has completed would stop further damage to data, without salvaging any already lost.
Security experts have suggested precautionary measures for dealing with ransomware. Using software or other security policies to block known payloads from launching will help to prevent infection, but will not protect against all attacks As such, having a proper backup solution is a critical component to defending against ransomware. Note that, because many ransomware attackers will not only encrypt the victim's live machine but it will also attempt to delete any hot backups stored locally or on accessible over the network on a NAS, it's also critical to maintain "offline" backups of data stored in locations inaccessible from any potentially infected computer, such as external storage drives or devices that do not have any access to any network (including the Internet), prevents them from being accessed by the ransomware. Moreover, if using a NAS or Cloud storage, then the computer should have append-only permission to the destination storage, such that it cannot delete or overwrite previous backups. According to comodo, applying two Attack Surface Reduction on OS/Kernel provides a materially-reduced attack surface which results in a heightened security posture.
Installing security updates issued by software vendors can mitigate the vulnerabilities leveraged by certain strains to propagate. Other measures include cyber hygiene − exercising caution when opening e-mail attachments and links, network segmentation, and keeping critical computers isolated from networks. Furthermore, to mitigate the spread of ransomware measures of infection control can be applied. Such may include disconnecting infected machines from all networks, educational programs, effective communication channels, malware surveillance and ways of collective participation
File system defenses against ransomware
A number of file systems keep snapshots of the data they hold, which can be used to recover the contents of files from a time prior to the ransomware attack in the event the ransomware does not disable it.
On Windows, the Volume shadow copy (VSS) is often used to store backups of data; ransomware often targets these snapshots to prevent recovery and therefore it is often advisable to disable user access to the user tool VSSadmin.exe to reduce the risk that ransomware can disable or delete past copies.
On Windows 10, users can add specific directories or files to Controlled Folder Access in Windows Defender to protect them from ransomware. It is advised to add backup and other important directories to Controlled Folder Access.
Unless malware gains root on the ZFS host system in deploying an attack coded to issue ZFS administrative commands, file servers running ZFS are broadly immune to ransomware, because ZFS is capable of snapshotting even a large file system many times an hour, and these snapshots are immutable (read only) and easily rolled back or files recovered in the event of data corruption. In general, only an administrator can delete (but cannot modify) snapshots.
File decryption and recovery
There are a number of tools intended specifically to decrypt files locked by ransomware, although successful recovery may not be possible. If the same encryption key is used for all files, decryption tools use files for which there are both uncorrupted backups and encrypted copies (a known-plaintext attack in the jargon of cryptanalysis. But, it only works when the cipher the attacker used was weak to begin with, being vulnerable to known-plaintext attack); recovery of the key, if it is possible, may take several days. Free ransomware decryption tools can help decrypt files encrypted by the following forms of ransomware: AES_NI, Alcatraz Locker, Apocalypse, BadBlock, Bart, BTCWare, Crypt888, CryptoMix, CrySiS, EncrypTile, FindZip, Globe, Hidden Tear, Jigsaw, LambdaLocker, Legion, NoobCrypt, Stampado, SZFLocker, TeslaCrypt, XData. The No More Ransom Project is an initiative by the Netherlands' police's National High Tech Crime Unit, Europol’s European Cybercrime Centre, Kaspersky Lab and McAfee to help ransomware victims recover their data without paying a ransom. They offer a free CryptoSheriff tool to analyze encrypted files and search for decryption tools.
In addition, old copies of files may exist on the disk, which has been previously deleted. In some cases, these deleted versions may still be recoverable using software designed for that purpose.